In the ever-changing realm of cybersecurity, where risks are in constant flux, businesses face the challenge of reinforcing their defenses. Safeguarding sensitive data and ensuring seamless operations requires a comprehensive defense strategy. This exploration of proactive firewall monitoring reveals its vital role in business security, from early threat detection to the meticulous efforts of cybersecurity teams. Traverse through the layers of this security landscape, shedding light on the critical aspects of effective cybersecurity solutions.
Embark on a journey through the intricacies of proactive firewall monitoring, uncovering the elements that construct a robust shield against cyber threats. Gain insights into not just the ‘what’ and ‘why’ but also the ‘how’ behind effective firewall monitoring, empowering businesses to navigate the digital landscape securely.

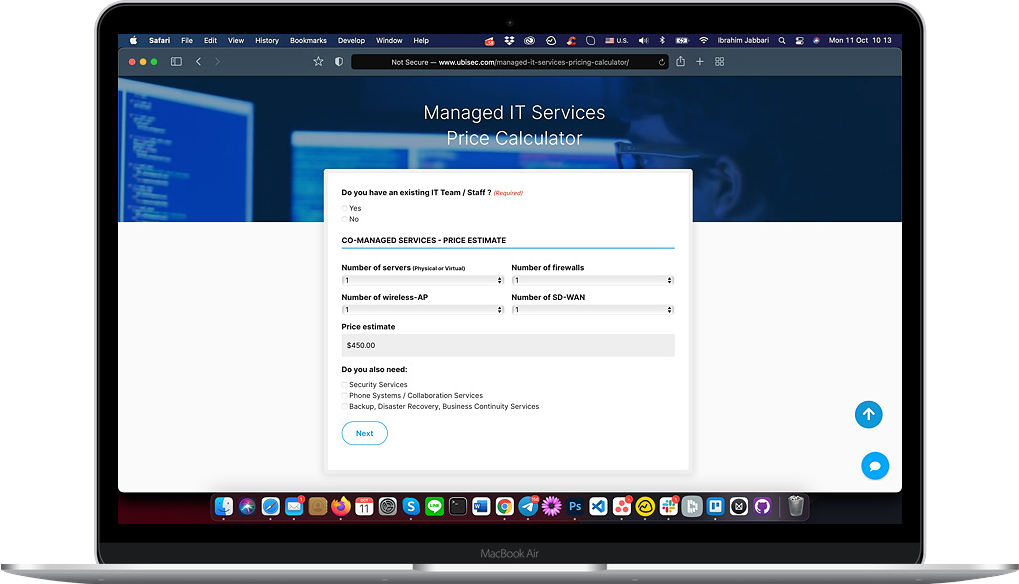
Firewall Monitoring, In A Nutshell
The Need for Proactive Firewall Monitoring
Early Detection of Security Threats
Identification of Vulnerabilities
Proactive monitoring of a firewall helps in identifying and addressing security vulnerabilities. It can highlight areas of the network that are prone to attacks, enabling the IT team to strengthen these weak points. Without proactive monitoring, these vulnerabilities might go unnoticed, leading to potential security breaches.
Compliance with Security Standards
Engaging in proactive monitoring of your firewall is vital for upholding compliance with security standards and regulations, especially for businesses managing sensitive customer data. Failing to comply can result in legal repercussions and harm to the company’s reputation.
Continuous Improvement of Security Measures
Ensuring Business Continuity
By detecting and resolving security threats early, proactive firewall monitoring helps ensure business continuity. Downtime due to security breaches can be costly and disruptive. If you’re not proactively monitoring your firewall, you might only know about a security breach once it’s too late, resulting in considerable downtime and potential loss of business.
Are you aware of the latest cybersecurity threat circling your business? Click here to learn more!

Threats: Navigating the Complex Landscape
Potential Threats
Potential threats loom in the digital shadows, waiting to exploit vulnerabilities in network defenses. These can range from seemingly innocuous activities to sophisticated attacks. It’s imperative to recognize potential threats early on to preemptively secure the digital perimeter.
Detection:
- Anomaly Detection: Firewalls employ sophisticated anomaly detection mechanisms to identify unusual patterns or behaviors within network traffic.
- Behavioral Analysis: Monitoring and analyzing the behavior of network entities helps detect deviations from established norms, signaling potential threats.
Potential Security Threats
Potential security threats pose a risk to the integrity of a system or network, potentially leading to data breaches or service disruptions. Identifying and mitigating potential security threats is a proactive measure to prevent severe consequences.
Detection:
- Intrusion Detection Systems (IDS): Employing IDS, firewalls can identify and alert administrators to potential security threats, enabling rapid response.
- Security Audits: Regular security audits help assess vulnerabilities and anticipate potential security threats before they manifest.
Security Threats
Security threats encompass a broad spectrum of malicious activities, ranging from malware and phishing attacks to unauthorized access attempts. Recognizing these threats is fundamental to implementing effective countermeasures.
Detection:
- Signature-Based Detection: Firewalls use predefined patterns or signatures to identify known security threats, such as malware or specific attack types.
- Packet Filtering: Analyzing packets of data for specific characteristics enables firewalls to block or allow traffic based on predefined security rules.
External Threats
External threats originate from sources outside the internal network, often posing substantial risks to overall cybersecurity. Shielding against external threats requires a robust defense strategy and constant vigilance.
Detection:
- Geolocation Filtering: Restricting access based on the geographical location of incoming traffic helps mitigate external threats.
- Threat Intelligence Feeds: Integration of threat intelligence feeds enables firewalls to stay updated on the latest external threats and adapt their defenses accordingly.

The Role of Cybersecurity Team in Proactive Firewall Monitoring
Identification of Potential Threats
The cybersecurity team is consistently engaged in monitoring the firewall to pinpoint potential threats or irregularities within the network. Employing advanced tools and techniques, they scrutinize for unusual traffic patterns or data transfers that could signify a security breach.
Quick Response to Security Incidents
Actively monitoring the firewall proactively equips the cybersecurity team to respond to security incidents swiftly. Their capability to promptly isolate affected systems serves as a preventive measure, mitigating the potential spread of malware or other malicious activities.
Regular Firewall Updates and Patches
Maintaining a proactive stance, the team takes responsibility for regularly updating the firewall with the latest patches and security fixes. This diligence is paramount in fortifying defenses against emerging cyber threats and vulnerabilities.
Compliance with Security Policies and Regulations
Consistent firewall monitoring plays a pivotal role in enabling the cybersecurity team to uphold compliance with company security policies and industry regulations. This practice ensures a comprehensive record of network activity, facilitating audits and investigations when needed.
Prevention of Downtime and Business Disruptions
Taking a proactive stance with firewall monitoring is instrumental in averting downtime and disruptions caused by cyber-attacks. The cybersecurity team’s ability to swiftly respond allows for timely intervention, effectively mitigating the impact of security incidents and ensuring seamless business continuity.
Do you need a quick assessment to check your cybersecurity posture? Look no further, click here to learn more!
Conclusion
Recognizing the significance of proactive firewall monitoring is crucial for businesses dedicated to securing their networks and safeguarding sensitive data. With a wealth of expertise in cybersecurity solutions, Ubisec Systems presents tailored firewall tracking services crafted to guarantee the security and uninterrupted flow of your business operations. The urgency is apparent—waiting for a security breach is not an option. Take proactive measures today to fortify your business with the specialized services offered by Ubisec Systems.
Contact Ubisec Systems today to enhance your firewall monitoring and secure your business against evolving cyber threats. Let us be your partner in creating a robust cybersecurity strategy. Click here to get started!
FAQs
What is a firewall monitor?
A firewall monitor is a tool or system that continuously observes and analyzes the activities within a firewall to identify and respond to potential security threats.
What is the purpose of a firewall?
Engaging in proactive firewall monitoring serves as a proactive measure to thwart downtime and business disruptions resulting from cyber-attacks. The cybersecurity team’s ability to swiftly intervene and mitigate the impact of security incidents ensures seamless business continuity.
How does a firewall work?
A firewall works by examining and controlling the flow of data entering and leaving a network based on predefined security rules. It acts as a barrier, allowing or blocking data packets according to these regulations to prevent unauthorized access and protect against security threats.
Can a firewall monitor CPU usage?
While firewalls primarily focus on monitoring network traffic, some advanced firewalls may have the capability to monitor CPU usage to identify unusual patterns that could indicate a potential security threat.
How does a firewall help in monitoring the network?
A firewall helps in monitoring the network by analyzing incoming and outgoing traffic, identifying potential threats, and enforcing security rules. It provides visibility into network activities, allowing for the detection and prevention of security breaches.